VPN Service Hijacked

Recently one of the most popular free VPN services was hijacked by hackers. Tor networks are used by tens of thousands of internet users daily in the US, and into the millions worldwide as a way to remain anonymous and secure when using the internet.
VPN services are generally billed as the best way to maintain internet security when traveling. Yet, during this incident, like several previous incidents, the hackers actually used software that unsuspecting users thought would secure them to exploit them.
What Is VPN?
If you are not familiar with VPN services or why you might need one, we suggest jumping over and checking out our article on WiFi Risks and Prevention and How Travel Routers Secure WiFi for more about the risks, guidance and solutions.
VPN stands for virtual private network. A VPN service will add an additional layer of encryption to your internet use. It secures the connection and creates what is called a “tunnel”.
Because the network the VPN creates is private, it will hide and isolate your information and internet contents from other devices or users on WiFi. They won’t even be aware it exists and it will be encrypted so even if they do discover it, they won’t be able to read its contents.
How Travel Routers Secure WiFi
Tor VPN is also one of several open source VPN services. Open Source in technology terms mean community provided, or crowdsourced. They are popular because they are often free, and community supported which means there is often lots of support. However, because they are provided by the community, rather than a company or organization they also may have limited oversight.
What Happened
Hackers in August hijacked what are known as exit relays for Tor’s VPN service. Exit relays are like off ramps of a highway. It’s the point where the data you send from your device leaves the private tunnel of the VPN service and goes back into the public internet.
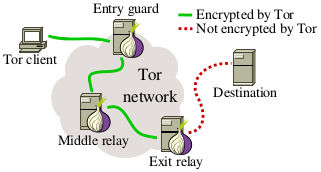
The hackers essentially created a new end of the tunnel that they controlled. As the secure traffic came out, they were able to easily see all of the data coming through, because they controlled the exit. Instead of the data being secured, it was sent right to the hackers. And even worse, because they appeared to be part of the secure network, they were given the key to unlock of the information.
These “relays” are known as onions in the Tor Community. When they are compromised they become known as “spoiled onions”. For the average user, what matters is that if you use Tor, or the VPN service you use uses Tor, you may unsuspectingly wind up interacting with one of these spoiled onions. If you do, your information could easily be compromised.
While the hackers primarily targeted financial information, and specifically seemed to focus on Bitcoin, it does illustrate some of the flaws with free and crowdsourced VPN services. Tor is an open source VPN system and that presented opportunities to be hijacked.
This Isn’t The First Time
This actually isn’t the first time, Tor and other free open source VPN networks have been hacked numerous times. In fact, there have been more than a dozen published hijacks of free VPN services since 2011. Since these are just the published hacks and hijacks, there have likely been countless other smaller incidents and occurrences.
While free is always compelling from a value proposition standpoint, the crowdsourced and community nature of open source systems leaves them as prime opportunities for hackers and hijackers.
What It Means For You
For the average user there are a handful of take aways from this experience. While Tor and other free VPN have value, if you are looking to remain secure when traveling we have the following recommendations and considerations:
1. Free security is generally limited security
There are few free security services that are as capable as paid services. A paid service business won’t stay in business long if they are constantly subjected to hacks and hijacks. There is simply a lot of motivation for a business to protect its users when that is part of its core business. While this is absolutely true with any type of security, its particularly true of internet security.
Free security should never assumed to be totally secure, especially when it is “open source”.
2. Financial Information And Transactions Are Targets
While there are numerous reasons to use VPNs and internet security, one common reason is to protect against hijacks targeted towards financial information and transactions. Even when using security software, take extra care when using financial systems and networks. Bitcoin is particularly compelling to hackers because it is easily used throughout the world with little protection.
We always recommend avoiding free systems and networks when using sensitive transaction systems.
3. Anonymity Shouldn’t Be Confused With Security
While Tor VPN and other VPN services can be secure, the focus of most open source VPN services are not security, but rather anonymity. Anonymity is the ability to remain unknown to destination websites. Using free VPN and anonymity services should following rules #1 and #2 which is to assume that they are never totally secure and sensitive transactions should be avoided.
Bottom line: Anonymity is not the same thing as security.
